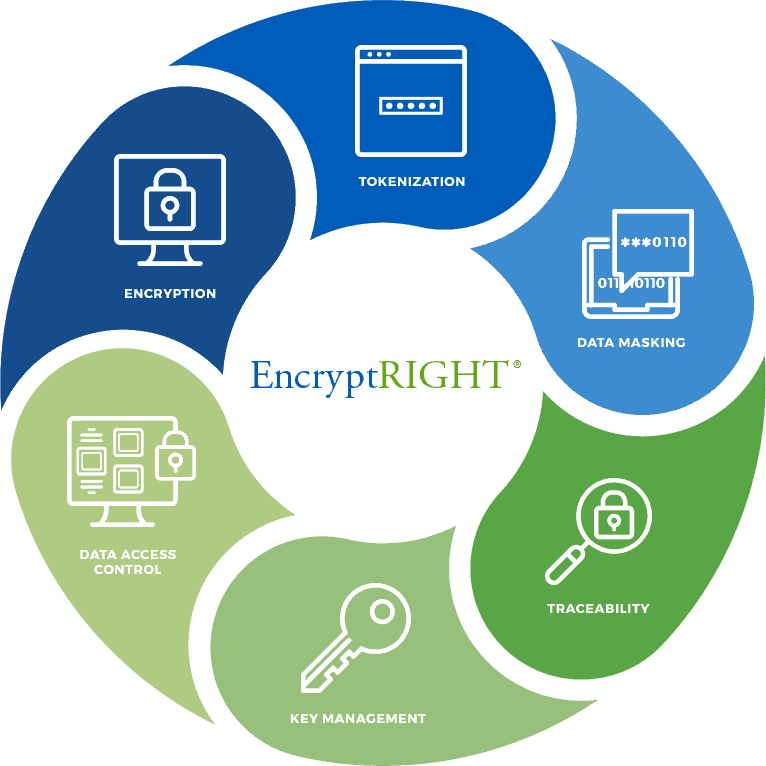
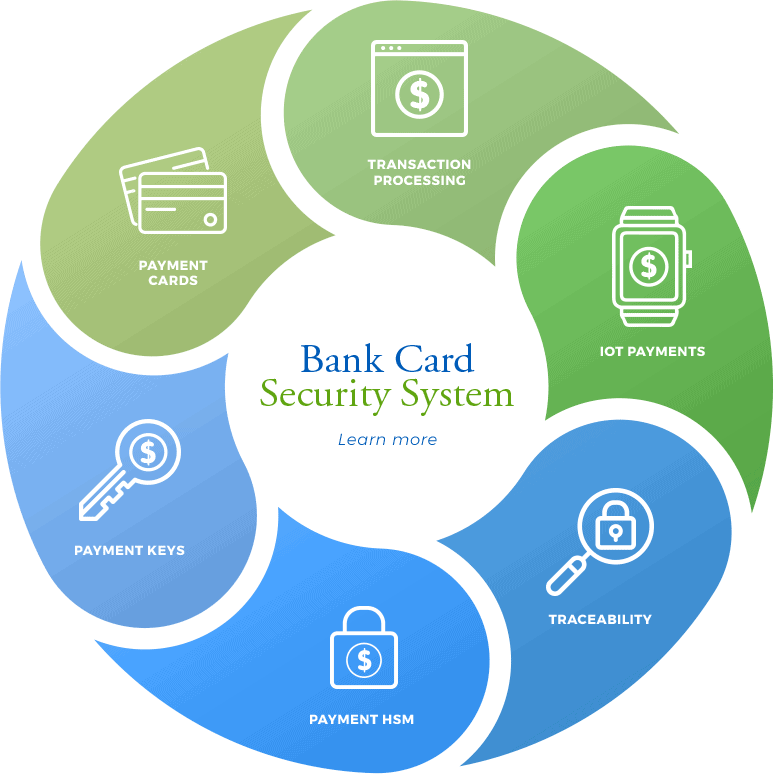
Every day, businesses share sensitive information outside the enterprise, such as sending purchasing files or other documents containing personally identifiable information to trading partners, resellers, or third parties. Safeguarding this data is crucial to avoid a breach and comply with regulations, which is why organizations often implement file encryption infrastructure to keep sensitive information secure […]