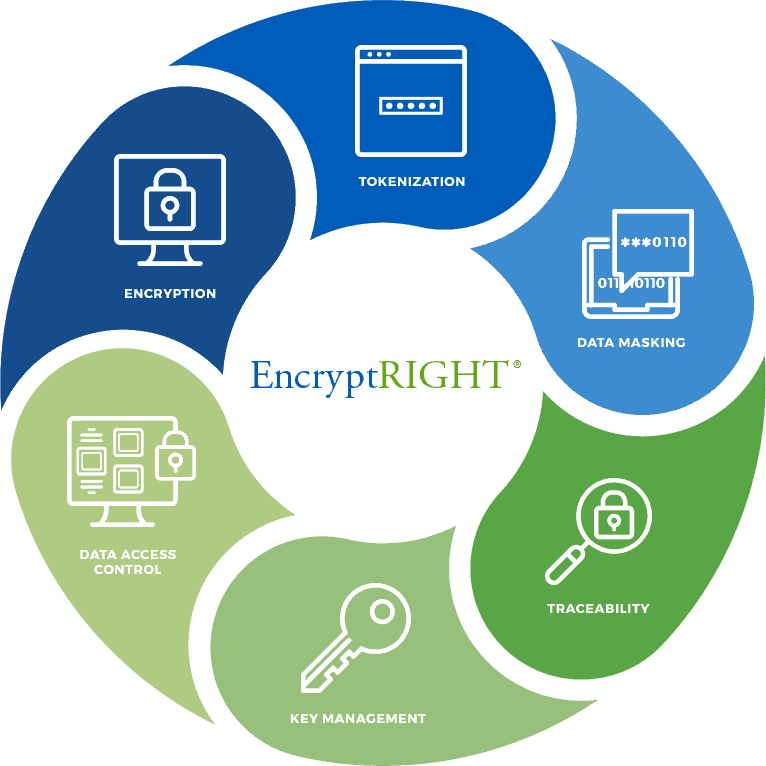
EncryptRIGHT is the leading data security platform that simplifies application layer encryption and data protection by abstracting data protection policies from application programming, while providing a complete separation of duties between information security and application programming. EncryptRIGHT defines and enforces how data is protected, who may access specific data, and what format that data will take when access is granted (unrestricted, partially masked or fully restricted).

Pseudonymize and Anonymize sensitive data for regulatory and industry standards compliance
Learn More
Enable data privacy with dynamic data masking and role-based access controls
Learn More
Control who can access sensitive data and to what degree; full, partial, or no access
Learn More
Implement & Automate Data Protection Policies to encrypt data at the application level
Learn MoreData secured, privacy ensured and compliance mandates met. EncryptRIGHT.
A unique Data-Centric Security Architecture allows information security teams to comprehensively define an EncryptRIGHT Data Protection Policy (DPP) and to bind the policy to data itself, protecting it regardless of where the data is used, moved or stored. Programmers do not need to have cryptography expertise to protect data at the application layer – they simply configure authorized applications to call EncryptRIGHT and ask for data to be appropriately secured or unsecured in accordance with its policy. EncryptRIGHT protects the data at the application layer with the encryption or tokenization techniques, formats and methodologies defined in the data protection policy. Role-based access controls are applied to unsecure data in the exact format authorized for specific applications or users – fully restricted, unrestricted or partially concealed with the appropriate data mask dynamically applied. Managing cryptographic keys in and across applications can be very complicated, but EncryptRIGHT centralizes and automates cryptographic key management.
Application native data protection, in as little as 3 lines of code.

Data protection policies are automatically and uniformly enforced, and built-in audit and reporting functionality provides traceability and alerting to assure that data is secured, privacy is protected, and compliance is met. Support for a variety of interfaces, from COBOL to C# and Java, from CLI to Web API, allows programmers to connect using the interfaces with which they are most comfortable, and out-of-the-box functionality for every common enterprise operating system, from IBM mainframe to Windows, means less customization and quicker implementations wherever enterprise applications run, on premise or in the cloud. With EncryptRIGHT, protecting data where it is most exposed and susceptible to risk has never been so easy.
