EncryptRIGHT software delivers strong data security with a primary focus on application level data encryption, and also supports encrypting databases with transparent data base encryption (TDE) and encrypting files for transfer or backup, protecting sensitive data regardless of where it is used, moved or stored.
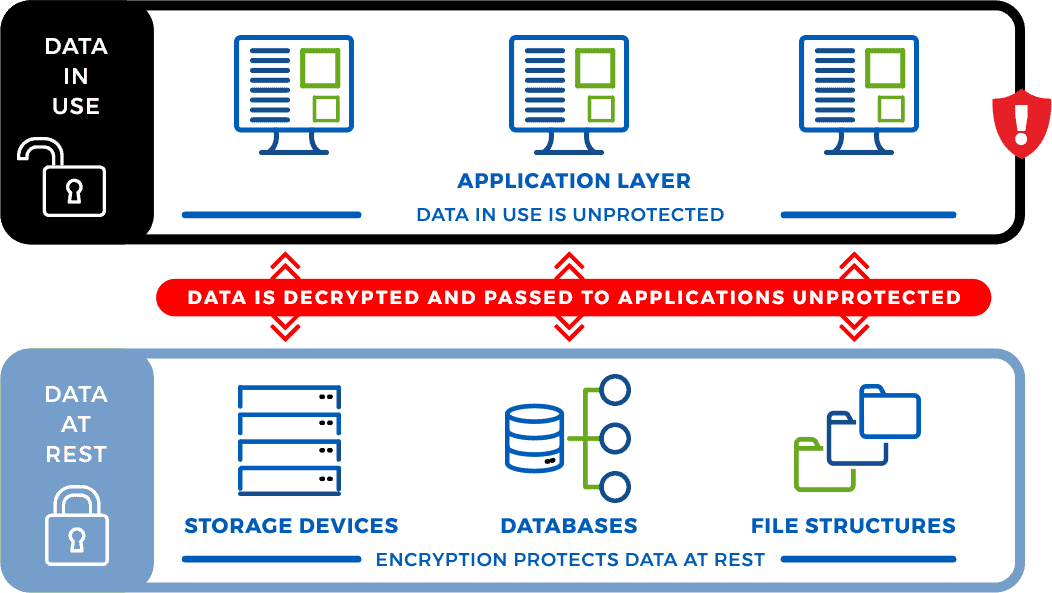
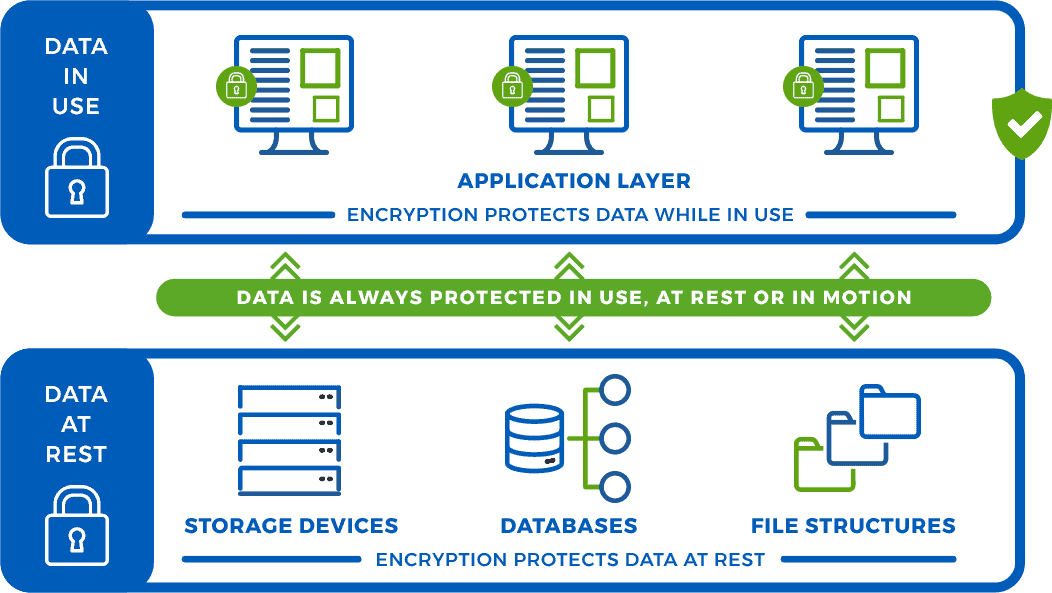
Application Level Data Encryption is considered the most secure approach to enterprise data protection. When sensitive data is encrypted at the application level data, it becomes inherently protected wherever it is – in applications, on disks, in file structures or databases, or being transported through a network.
Most data is established in an enterprise through an application, either through import or generation, and when application level encryption is applied, the data is secured before it leaves an application. Whether the data is transported to a third party, stored on a backup disk, placed into a file or database, or handed off to another application, the data is always secure. Traditional data protection software solutions encrypt data while at rest, but often leave it unprotected in the clear when it is being used by an application, leaving it vulnerable to a data breach. While the traditional approach to application level data protection is considered by many to be too complex to be practical, EncryptRIGHT simplifies application level data protection.