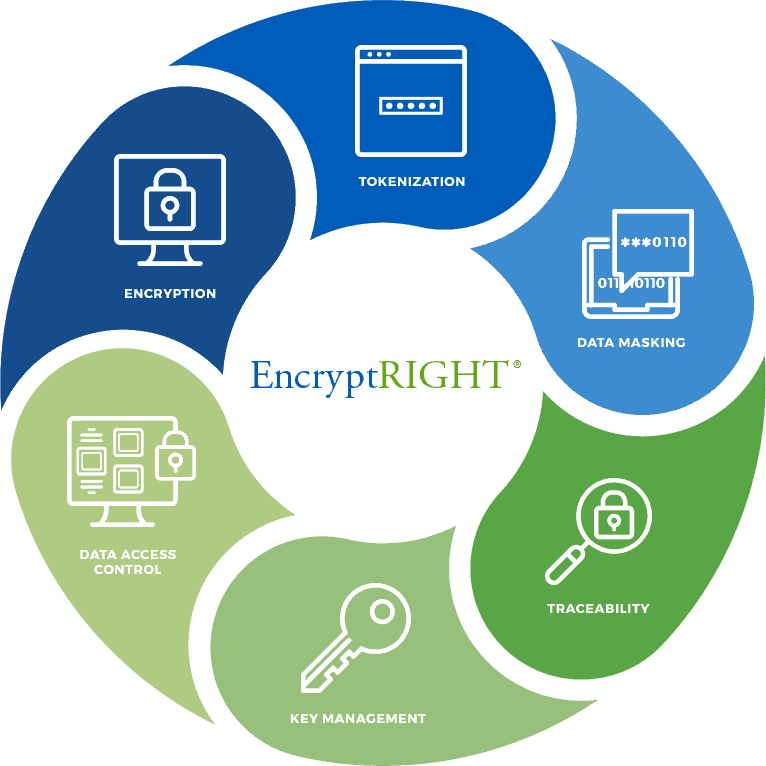
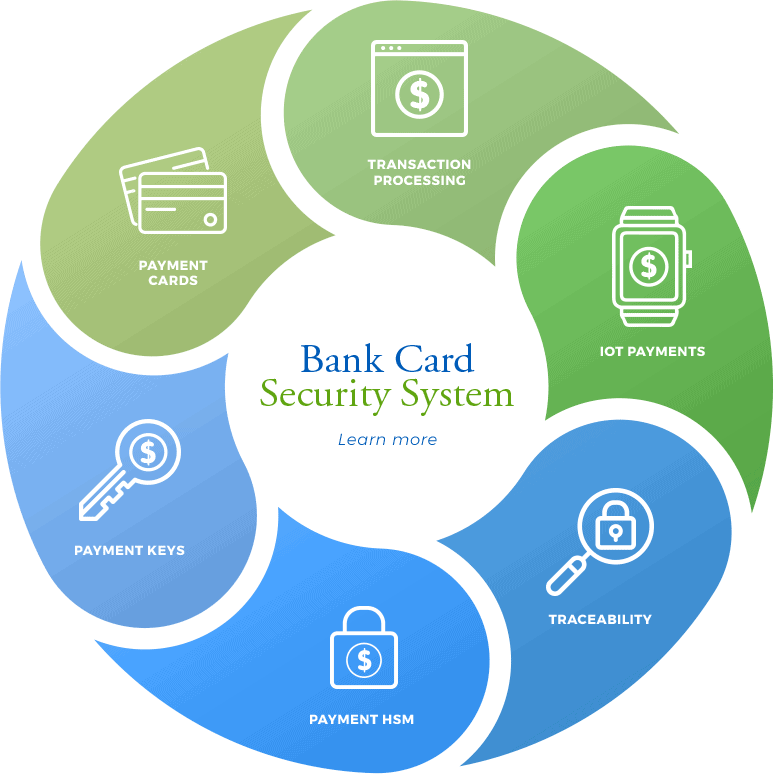
As digital systems proliferate, the need to address evolving threats to critical data becomes increasingly urgent. Implementing a crypto-agile architecture is essential for organizations striving to adapt to ever-changing security challenges and regulatory demands. However, deploying such an architecture across existing environments can be challenging and requires a methodical approach to ensure robust security and […]